Upcoming events
Upcoming events
Past

12-14 September, 2022
ML techniques for IoT, security threat prediction, and threat prevention
Understanding how to use existing Machine Learning techniques (Supervised, Unsupervised, Reinforcement Learning) and Libraries to implement make a machine Learning model. Design an ML model to distinguish between IoT and non-IoT devices. Understanding how we use machine learning to predict malware and benign files.
Understanding the development and deployment of machine learning models for detecting IoT DoS and DDoS Attacks. ML-specific Threats and their Mitigations” provides details on specific attacks as well as specific mitigation steps used today to protect products and services against these threats.
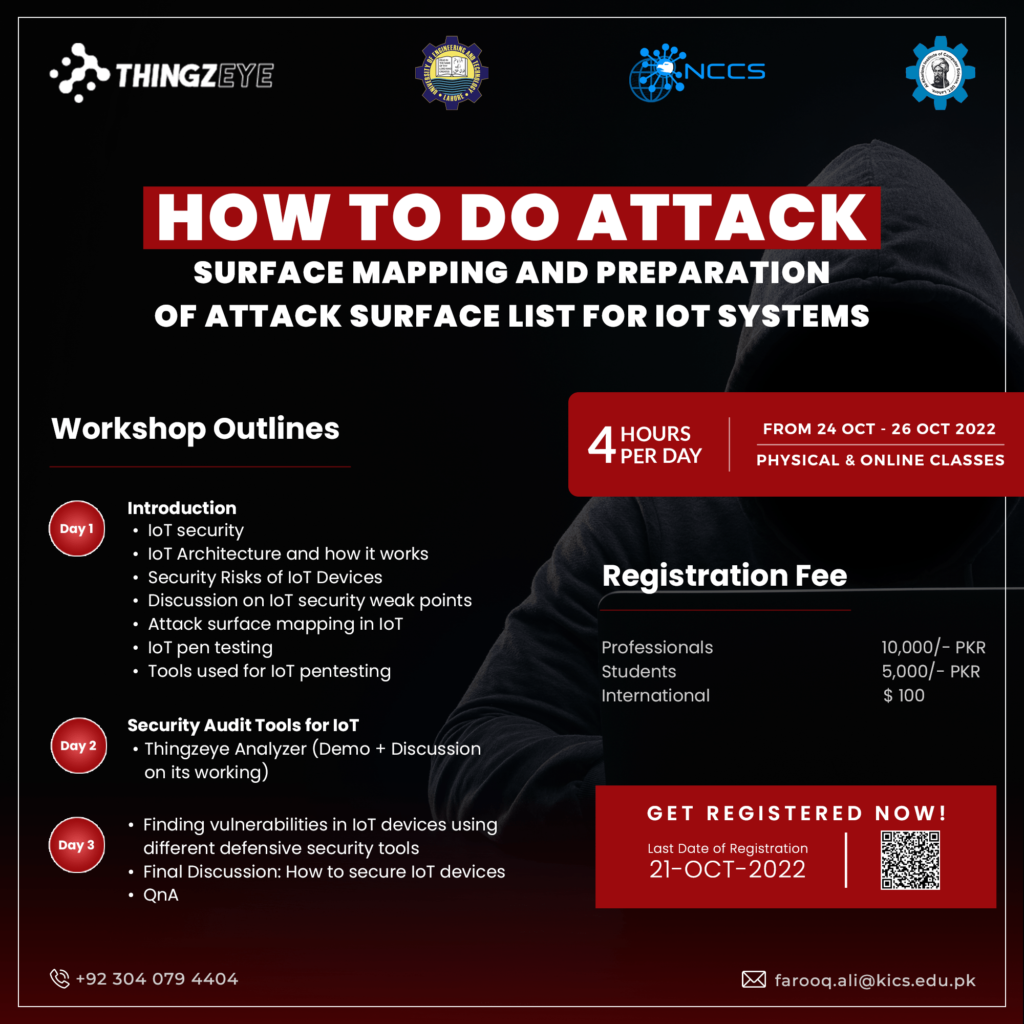
24-26 October, 2022
How to do attack surface mapping and preparation of attack surface list for IoT systems
The goal of this workshop is to provide the attendees with the basic knowledge of IoT attacks vulnerabilities and risks and to give them basic understanding of how they can protect their IoT systems.
Specifically, network attack surface mapping will be covered with demonstration of examples. In addition to that they will get to know about the importance of securing the IoT attack surface areas. This learning will aid them in securing their IoT system by keeping in mind the IoT security goals.

21-23 November, 2022
Ethical hacking of IoT devices
- A basic knowledge of IoT hacking and how IoT devices are designed to
work and how to protect your infrastructure with these devices coming
online - Plan a vulnerability assessment and penetration test for IoT
- Execute an offensive penetration test using standard hacking tools in an ethical manner.
- Finally performing offensive ethical attacks against IoT devices.

16-18 August, 2022
Implementation of security mechanisms/protocols with different layers of IoT protocol
- Understanding of Implementation of security mechanisms/protocols with different layers of IoT protocol
- Understanding security challenges posed by the Internet of Things (IoT) systems, including IoT devices, IoT protocols, and their vulnerabilities
- Understanding of OneM2M Architecture Based Secure MQTT Binding in Mbed OS
- Understanding of Minimalist Implementation of oneM2M Security Architecture for Constrained IoT Devices
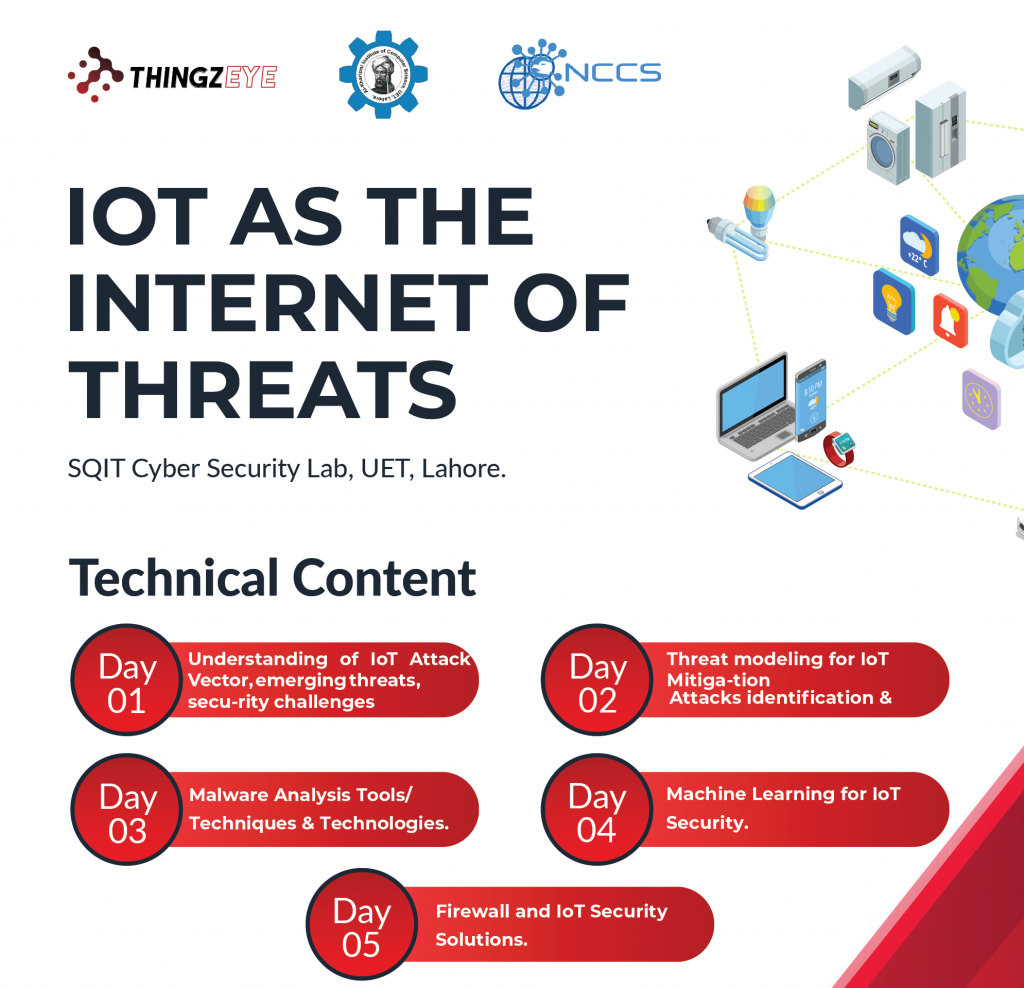
8 October, 2021
IoT as internet of threats
- Understanding of IoT Attack Vector, emerging threats, security challenges.
- Threat modeling for IoT Attacks identification & Mitigation.
- Malware Analysis Tools/ Techniques & Technologies.
- Machine Learning for IoT Security.
- Firewall and IoT Security Solutions.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
