Device static and dynamic vulnerability analysis
Firmware is the core of any embedded device whether it is IoT or any other embedded systems device. At the IoT security lab, we have experts who can perform both static and dynamic firmware analysis of IoT devices using our state-of-the-art tools ThingzAnalyzer, which is available online at www.analyzer.thingzeye.com, and ThingzAnalyzer Box. The team also has the strong hardware analysis skills to perform device hardware vulnerability analysis by identifying open hardware ports for potential threats in the form of accessing/writing firmware and configuration/security parameters of the device.
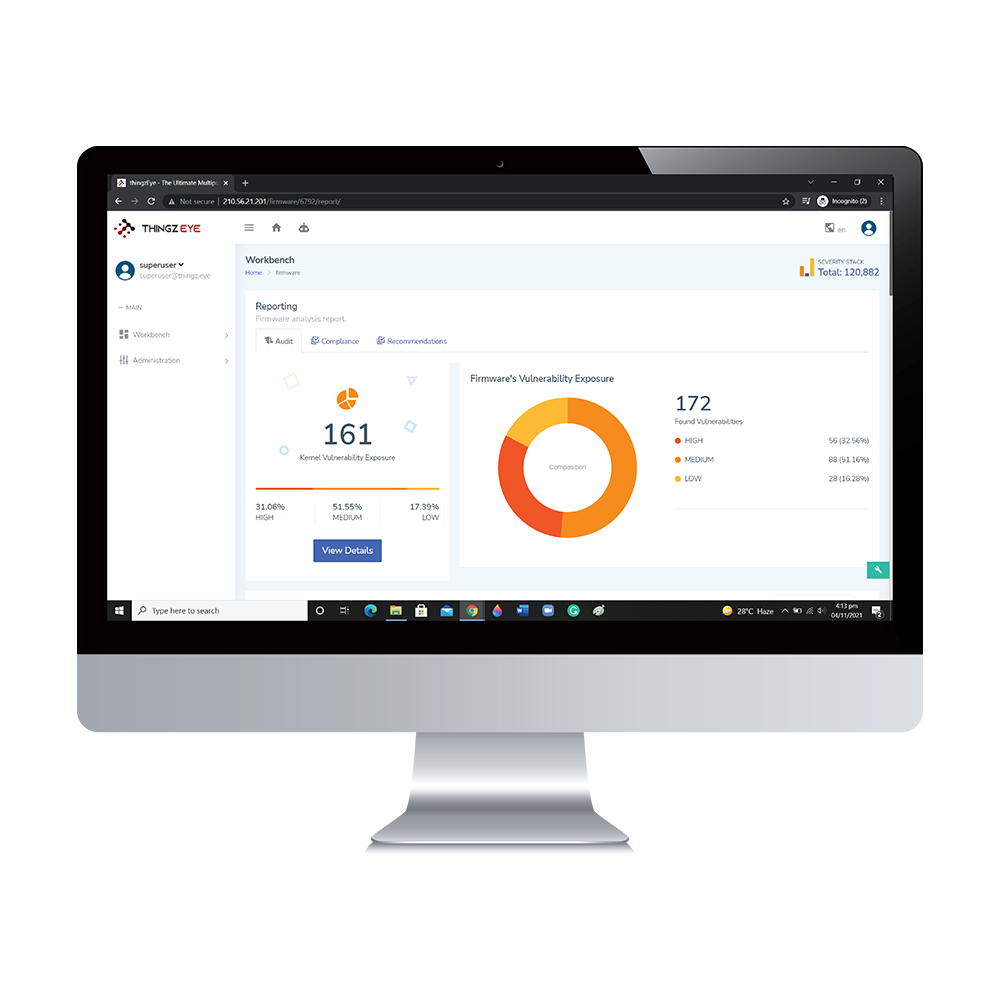
The ThingAnalyzer tool is also open for the users to perform their firmware scan free of cost. Users can sign in to our online Analyzer service and see the detailed report of the audit of the device or firmware as shown in the right pane. The first screen shows the summary of vulnerabilities found in different components of the firmware along with their severity level.
Static
This service includes our proprietary, audit tool which will perform the extraction of firmware and identification of key vulnerable components which include binaries, and 3rd party libraries which are prone to a cyber-attack. We will provide a complete report including a detailed vulnerability analysis of your device firmware. Our static firmware analysis tool is in accordance with the National Vulnerability Database (NVD). By extensive analysis of your firmware, we will also present recommendations and detailed proofs-of-concept for device vendors to improve the security of device firmware.

Dynamic
This service includes the identification of run-time vulnerabilities in firmware. We provide this service where there is an absence of physical access to the device. Our team of IoT security experts performs complete in-depth dynamic analysis on IoT device firmware. We will provide a complete report on the behavior of communication traffic, system calls of binaries, and much more.
