Penetration Testing
Our penetration testing service identifies security vulnerabilities in networks, systems, and IoT devices. Using both manual and automated techniques, we simulate real-world cyber attacks to expose weak points, ensuring your cybersecurity defences are robust. Our experts adhere to industry standards like OWASP, OSSTMM, and PTES to deliver customized solutions for network security, web, and mobile applications. We offer Blackbox and Whitebox testing, and provide detailed reports, helping you stay ahead of cyber threats while meeting your security goals.
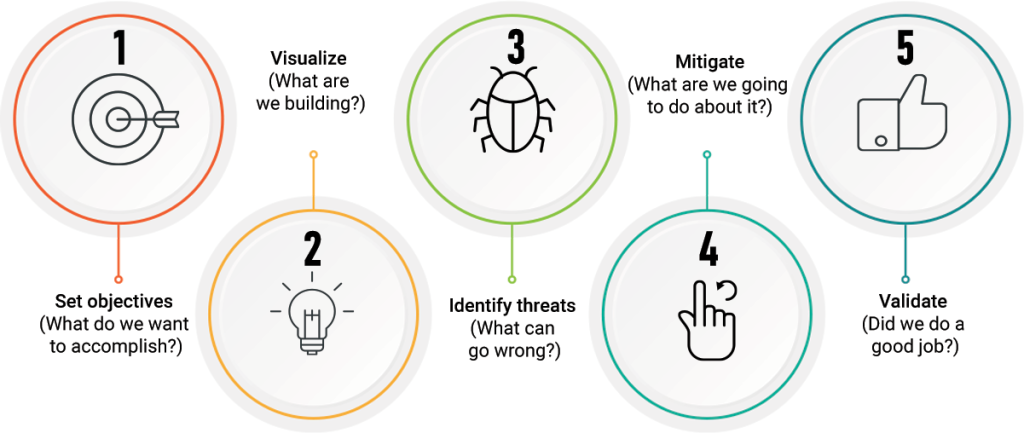
We will follow pentesting phases defined by NIST.
- Reconnaissance: This crucial phase of penetration testing helps identify hidden vulnerabilities and weaknesses in your network, ensuring comprehensive cyber security.
- Discovery and Scanning: Utilizing the gathered information, testers scan for open ports, services, and subdomains to assess potential security threats and network vulnerabilities.
- Vulnerability Assessment: A detailed vulnerability assessment reveals potential weaknesses that cyber attackers could exploit, securing your environment.
- Exploitation: Testers actively exploit identified vulnerabilities to simulate real-world attacks.
- Reporting: Detailed reports offer insights into cyber security threats, test results, and recommended solutions.
Penetration Testing Scope:
The scope of pentesting can be defined after you meet with our experts. However, we can offer you services in the following areas:
- External Network
- Internal Network
- Wireless Interfaces
- IoT devices
- Web Application
- Cloud Infrastructure
- Android Application
Our core expertise is security analysis of IoT devices both hardware and software. Therefore, we offer 360 degree security analysis of IoT devices that includes;
- Firmware & Hardware Pen Testing
- Firmware Vulnerability Assessment
- IoT Security Compliance Audit
- Device Network Security Assessment
- Device Web/Mobile VA/PT
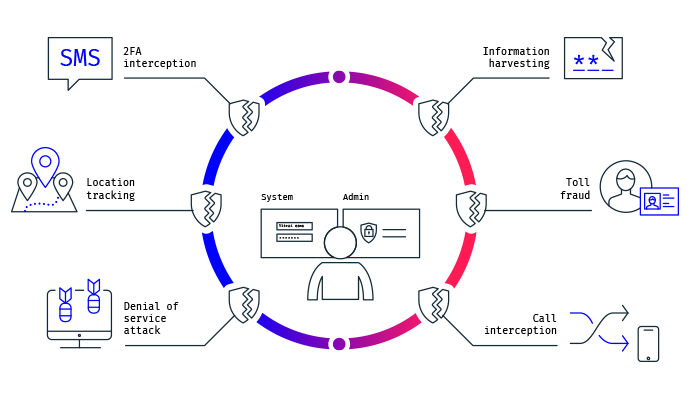
Threat Modeling
Threat modeling is a proactive cyber security approach to identify an organization’s security requirements, analyze potential cyber threats and vulnerabilities, assess risks, and suggest remediation steps. While penetration testing and secure code reviews help identify bugs in system implementations, threat modeling uncovers design flaws.
At ThingzEye, we utilize a threat modeling tool to simulate the system’s data flow diagram, following NIST, ISO, and IEC standards for IoT and industrial IoT systems. Our threat reports provide actionable insights to mitigate security vulnerabilities before system deployment.
For this, we evaluated our cyber security services on the Smart Grid system, identifying potential cyber threats and offering mitigation strategies through a comprehensive threat report. The report includes best practices in cybersecurity and solutions for maintaining reliable and secure energy flow in the Smart Grid.
We provide a complete cyber security solution for smart grid systems, addressing vulnerabilities during design and offering penetration testing and vulnerability assessments. Our enhanced ThingzModeler secures other IoT and Industrial IoT systems. Speak to our expert team for customized threat modeling services.
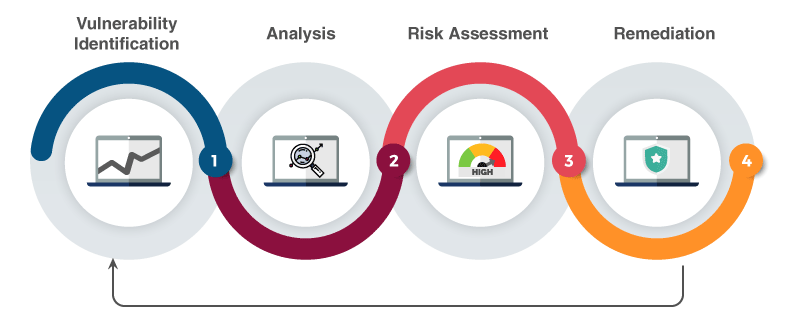
Device Static and Dynamic Vulnerability analysis
Firmware is the backbone of any IoT or embedded device. At the IoT Security Lab, our experts conduct both static and dynamic firmware analysis using advanced tools like ThingzAnalyzer (available at www.analyzer.thingzeye.com) and ThingzAnalyzer Box. We specialize in hardware vulnerability assessment by identifying open hardware ports that expose devices to cyber security threats.
ThingzAnalyzer is also accessible for users to perform free firmware vulnerability scans, providing detailed reports on security risks, threat levels, and device vulnerabilities.
Static
ThingzEye’s Static Firmware Analysis service uses a proprietary audit tool to extract and analyze firmware for vulnerabilities. By identifying risks in binaries and 3rd party libraries, we help mitigate cyber-attacks. Our analysis, aligned with the National Vulnerability Database (NVD), provides a detailed report with recommendations and proofs-of-concept to strengthen IoT device security. Improve your firmware’s resilience against security threats with our expert-driven static analysis.
Dynamic
Our dynamic analysis service identifies run-time vulnerabilities in IoT device firmware without requiring physical access. Leveraging our team of IoT security experts, we conduct comprehensive dynamic assessments to evaluate communication traffic and system call behaviors. Our detailed reports provide insights into potential cyber threats, ensuring robust security for your IoT solutions. Trust ThingzEye to enhance your firmware security through advanced vulnerability assessment and proactive threat modeling.
Embedded systems security and quality assurance
Embedded systems are integral to various IoT devices, and ThingzEye specializes in embedded systems security analysis. Our expert team conducts thorough security assessments, ensuring the integrity of hardware components and their configurations. In addition to embedded systems security, we offer comprehensive cyber security services, including vulnerability assessments, penetration testing, and firewall security, tailored to protect your IoT solutions and enhance network security. Discover our full range of services for robust cyber security solutions.
Developing Device Drivers
The experience of device drivers and porting for specific architecture has been our focus for the past few years. We have worked on the development and integration of drivers for various interfaces such as UART, SPI, I2C, and USB to Serial.
Embedded Architectures
We have a workforce available specially for ARM, MPC and MIPS architecture based embedded devices.
Application Development
It consists of application development for real-time with multi-tasking, multi-processing, and scheduling. We have the expertise of working on the different embedded operating systems.
IoT Hardware vulnerability assessment
Securing IoT device hardware is crucial to prevent cyber-attacks that could compromise sensitive firmware and information. Our cybersecurity experts specialize in identifying vulnerabilities in debug ports and physical access points. We conduct comprehensive hardware assessments aligned with IoT NIST guidelines and OWASP standards, utilizing a security compliance checklist to detail identified vulnerabilities. Trust ThingzEye for robust IoT security solutions that protect your devices from emerging cyber threats and ensure compliance with industry best practices.

