Penetration Testing
Penetration testing is a process of identification of security weaknesses in which a cyber-security expert attempts to find and exploit vulnerabilities in a computer system with the consent of the system owner. The security expert may perform the simulated attack to identify any weak spots in a system’s defenses that attackers could take advantage of. The system under study may vary in terms of network topology, hardware, applications, services, and users, therefore our expert will design the customized penetration testing techniques according to your requirements. Our experts will realize how to help your organization’s security by searching for critical security loopholes in Network, Web, Mobile, and IoT. We can facilitate your needs using both manual and automatic testing approaches with our state-of-the-art techniques. We follow OWASP, OSSTMM, PTES, and EC Council standards to perform penetration testing of the organizations.
We perform both Blackbox and Whitebox penetration testing and define boundaries during our initial call and set a goal according to the information stakeholders provide. You can sit back and relax while we will do the critical task for you. As a result of the pentesting, you will be provided with a comprehensive report based on the audience (technical and managerial).
We will follow pentesting phases defined by NIST.
- Reconnaissance: The reconnaissance stage is crucial to thorough security testing because penetration testers can identify additional information that may have been overlooked, unknown, or not provided.
- Discovery and Scanning: The information gathered is used to perform discovery activities to determine things like ports and services that were available for targeted hosts, or subdomains, available for web applications.
- Vulnerability Assessment: A vulnerability assessment is conducted in order to gain initial knowledge and identify any potential security weaknesses that could allow an outside attacker to gain access to the environment or technology being tested.
- Exploitation: The exploitation phase takes care of exploiting all the vulnerabilities found during the previous step.
- Reporting: The report shows and explains the results of your tests and is the actual deliverable of your professional engagement.
Penetration Testing Scope:
The scope of pentesting can be defined after you meet with our experts. However, we can offer you services in the following areas:
- External Network
- Internal Network
- Wireless Interfaces
- IoT devices
- Web Application
- Cloud Infrastructure
- Android Application
Our core expertise is security analysis of IoT devices both hardware and software. Therefore, we offer 360 degree security analysis of IoT devices that includes;
- Firmware & Hardware Pen Testing
- Firmware Vulnerability Assessment
- IoT Security Compliance Audit
- Device Network Security Assessment
- Device Web/Mobile VA/PT
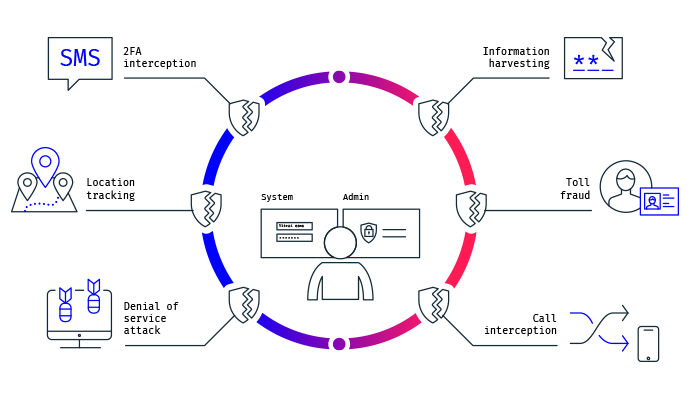
Threat Modeling
Threat modeling is a proactive security approach to identify the cyber security requirements of an organization, analyze the potential security threats and vulnerabilities risks, quantify threat and vulnerability criticality, and pinpoint the remediation steps. Penetration testing and code reviews can’t substitute for threat modeling. Penetration testing and secure code review are two activities that are effective for finding bugs in the secure implementation of the system. However, threat modeling is better at uncovering the design flaws of the system.
We use a Threat Modeling tool to model the entire system by creating its template. By using the functionality of a threat modeling tool to catch potential threats, we give recommendations to mitigate these threats even before the system is physically deployed.
It first allows the users to generate the prototype of the system in the form of a data flow diagram and then finds the potential threats by simulating the data flow diagram. The simulation is performed based on security and privacy controls defined by NIST, ISO, and IEC standards that are specially developed for IoT and industrial IoT systems.
We find threats based on these standards and provide suggestions to mitigate the threats in the form of a threat report. The threat report can be viewed and evaluated by the relevant organization to note down and mitigate the potential threats in their system even before it is designed.
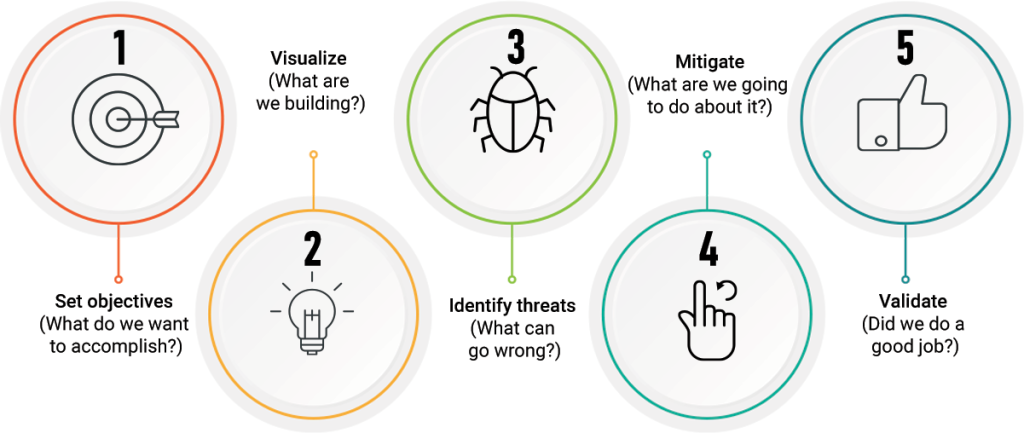
For this, we evaluated our service on the Smart Grid system that shows the potential threats and their mitigations in the form of a threat report. The threat report contains the best security practices and solutions that can be adopted for a Smart Grid System to provide a reliable and convenient flow of electricity to the consumers.
We give a complete security solution service for a smart grid system that helps identify and mitigate potential threats during the design phase of a smart grid and controls them after the system design. To provide augmented functionalities, we have further enhanced ThingzModeler for the security of other IoT and industrial IoT systems. We have developed threat modeling templates for many other industrial systems and are open to modeling any system. Please talk to our expert threat modeling team and they will guide you through the whole process.
Device Static and Dynamic Vulnerability analysis
Firmware is the core of any embedded device whether it is IoT or any other embedded systems device. At the IoT security lab, we have experts who can perform both static and dynamic firmware analysis of IoT devices using our state-of-the-art tools ThingzAnalyzer, which is available online at www.analyzer.thingzeye.com, and ThingzAnalyzer Box. The team also has the strong hardware analysis skills to perform device hardware vulnerability analysis by identifying open hardware ports for potential threats in the form of accessing/writing firmware and configuration/security parameters of the device.
The ThingAnalyzer tool is also open for the users to perform their firmware scan free of cost. Users can sign in to our online Analyzer service and see the detailed report of the audit of the device or firmware as shown in the right pane. The first screen shows the summary of vulnerabilities found in different components of the firmware along with their severity level.
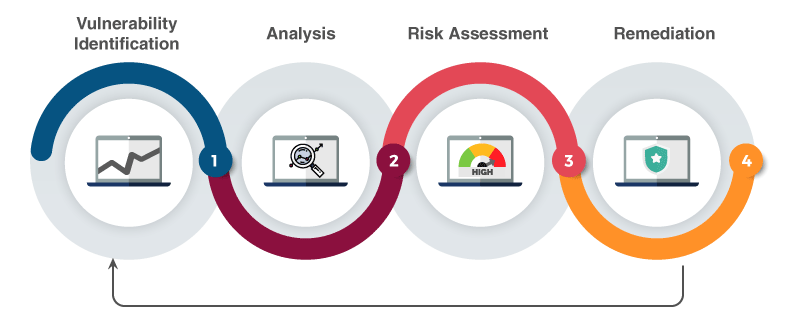
Static
This service includes our proprietary, audit tool which will perform the extraction of firmware and identification of key vulnerable components which include binaries, and 3rd party libraries which are prone to a cyber-attack. We will provide a complete report including a detailed vulnerability analysis of your device firmware. Our static firmware analysis tool is in accordance with the National Vulnerability Database (NVD). By extensive analysis of your firmware, we will also present recommendations and detailed proofs-of-concept for device vendors to improve the security of device firmware.
Dynamic
This service includes the identification of run-time vulnerabilities in firmware. We provide this service where there is an absence of physical access to the device. Our team of IoT security experts performs complete in-depth dynamic analysis on IoT device firmware. We will provide a complete report on the behavior of communication traffic, system calls of binaries, and much more.
Embedded systems security and quality assurance
Embedded systems include a variety of devices and IoT is one part of it. Our security experts can perform embedded systems security analysis. Our quality assurance feature will provide information on the hardware components of the device along with their configurations. Apart from these security services we also provide the following services.
Developing Device Drivers
The experience of device drivers and porting for specific architecture has been our focus for the past few years. We have worked on the development and integration of drivers for various interfaces such as UART, SPI, I2C, and USB to Serial.
Embedded Architectures
We have a workforce available specially for ARM, MPC and MIPS architecture based embedded devices.
Application Development
It consists of application development for real-time with multi-tasking, multi-processing, and scheduling. We have the expertise of working on the different embedded operating systems.
IoT Hardware vulnerability assessment
IoT device hardware is the physical layer that needs to be properly secured to avoid cyber-attacks which can provide the attacker access to the firmware of the device and other sensitive information. Our security experts will identify vulnerabilities in debug ports and physical access. We will perform a hardware assessment based on a security compliance checklist to provide a detail of identified vulnerabilities in hardware. Our compliance checklist is in accordance with IoT NIST guidelines and OWASP compliance standards.

